Account Creation Fraud prevention
Fraudulent account creation poses risks across various industries. E-commerce platforms often encounter attempts by fraudsters to create bogus accounts, aiming to exploit stolen credit card data or take advantage of promotional deals. Financial institutions, including banks and credit unions, are frequent targets, with fraudsters employing synthetic identities or stolen personal information to open unauthorized accounts. Similarly, gaming and gambling websites also experience account creation fraud, as fraudsters create fake accounts to exploit promotions, cheat, or engage in other fraudulent behaviors within the gaming community.
Account Creation Fraud checks
FrankieOne provides the following solutions that customer can use to prevent account creation fraud:
- Email check: Assesses whether the email is disposable, numeric, contains similarities to the user’s name, how new it is, how risky the domain is, and it’s general risk in Sardine’s network.
- Phone check: Assesses whether the number is associated with a VOIP (Voice over internet protocol), the risk of the carrier, whether the phone name matches the user's profile with their telco, or if it is reported as fraudulent.
- Device check: Assesses whether multiple customers are associated with a device or IP address, presence of emulators, proxies, or remote software.
- Behavioural biometrics: Assesses unusual activity such as lack of mouse movement on desktop devices, very fast sessions, screenshots taken, phone calls detected during sessions, multiple instances copy-pastes, and consistent phone orientation throughout the session.
- Location check: Assesses whether the user is located where they say they are, is using a VPN, or is in a high risk location.
Notes on the account creation solutions
Device, location, and behavioural biometric checks require the customer to integrate our OneSDK.
Entity status will only be Passed or Failed based on the results, there is no Needs Attention status.
Account creation fraud checks cannot be triggered from the Portal.
Email check
To ensure the security and integrity of user accounts, we implement a comprehensive email verification process to evaluate the potential risk associated with a user’s email address. By scrutinizing various aspects of the email, such as its domain reputation and any unusual patterns, we can effectively identify and mitigate risks before they impact our platform.
Phone check
The phone check is a critical security measure that evaluates the risk associated with a user’s phone number. This process involves rules designed to assess whether the phone number may be linked to fraudulent activities.
Device check
The device check is a robust mechanism designed to scrutinize a user’s device fingerprint. This process involves a set of rules meticulously crafted to assess the risk associated with a user’s device, thereby safeguarding against potential fraudulent activities and maintaining the integrity of the system.
Location check
The location check performs a set of rules designed to assess the risk associated with the user’s device location. This process helps in ensuring that the user is genuinely where they claim to be, providing an additional layer of security against fraudulent activities.
Behavioural biometrics check
The behavioral biometrics check assesses the risk associated with a user’s behavior during their interaction with a customer’s application. This evaluation helps identify any unusual or potentially fraudulent activity by monitoring various behavioral patterns, such as mouse movements, session durations, and interaction with the application.
Results in the Portal
The entity status will take the highest risk across all checks to determine the Entity Status result in the Portal.
Entity Status
If one of the checks (email, phone, device, and others) returns a high risk or very high risk, the status will be Failed.
When a user runs a recipe with account creation fraud checks, and it fails for any reason, they can see the specific risks associated with the failure on the overview page.
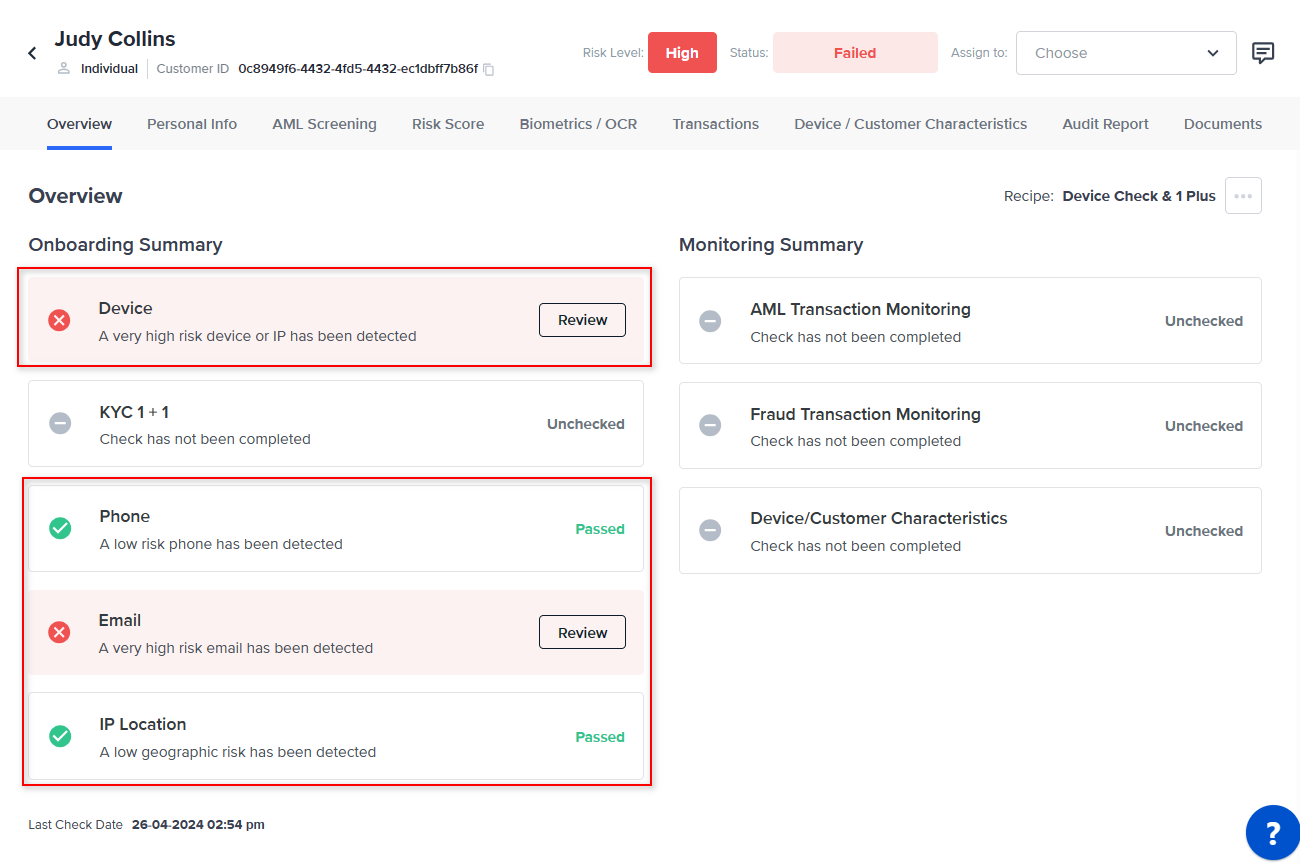
To view the details of any check that had risks detected, select the Review button.
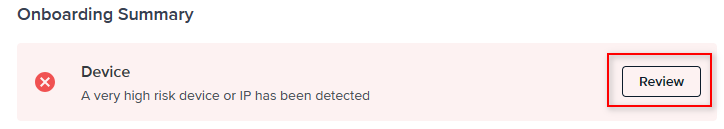
Alternatively, you can access the Personal Info tab and view the check result details.

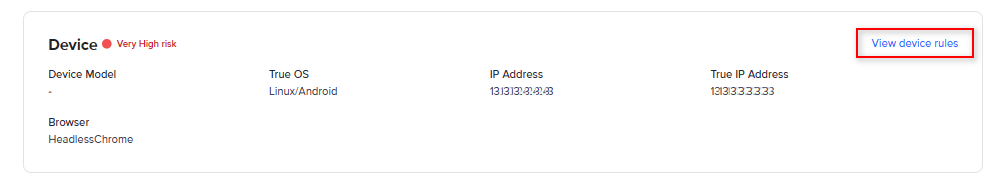
Each check results summary provides an overview of the information checked, and issues detected. There is also a link to display the rules that were applied on that specific check.
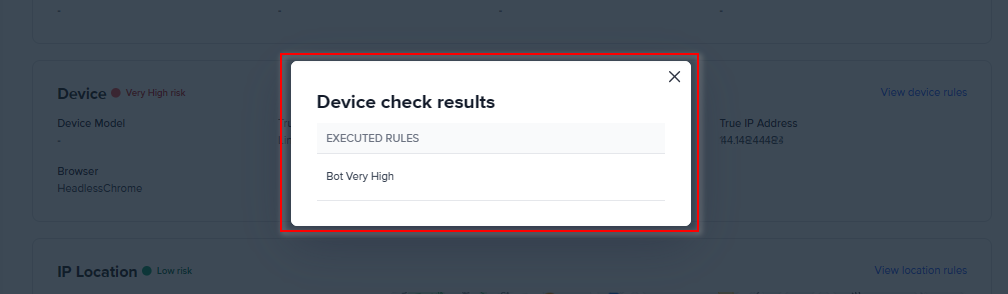
For example, for the for Device check results, you can select the View device rules link to open the rules that were run as part of the recipe and rulesets.
Updated 3 months ago
